Reinforcing Security of OT Systems in IIoT with MQTT and HiveMQ
In today's dynamic and increasingly complex field of industrial cybersecurity, the pursuit of communication protocols that are both efficient and secure is of utmost importance. MQTT — a streamlined and agile messaging protocol — is transforming the landscape of industrial data transmission and security. Initially designed for scenarios with constrained bandwidth, MQTT has quickly become a key component in the toolkit of Industrial IoT applications. This article explores MQTT's role in bolstering industrial security. It provides an overview of the challenges faced by Operational Technology (OT) teams and covers details on possible attacks. Finally, we share how HiveMQ can help mitigate threats that contemporary industries confront and reinforce communication security.
Cybersecurity Challenges of Operational Technology (OT) Systems
The cybersecurity challenges of Operational Technology systems are distinct and often more critical than those faced by traditional IT systems. OT systems, which control and monitor physical processes in industries, are increasingly becoming targets for cyber threats. Here are some specific cybersecurity weaknesses associated with OT systems:
Legacy Systems and Outdated Technology:
Many OT systems were designed and implemented before cybersecurity became a significant concern. This results in outdated technology with vulnerabilities that may not be easily patched or updated without disrupting critical processes.
Limited Security Standards:
Unlike the well-established cybersecurity standards in the IT domain, OT systems often lack universally accepted standards. The absence of standardized security measures can make it challenging to implement consistent and effective cybersecurity practices across different OT environments.
Convergence With IT Networks:
The integration of OT systems with IT networks, driven by the adoption of Industry 4.0 principles, creates new attack vectors. Cyber threats that penetrate the IT network may potentially propagate into the OT environment, posing serious risks to industrial control systems.
Insufficient Access Controls:
Weaknesses in access controls can allow unauthorized individuals or malicious actors to gain access to critical OT systems. Unauthorized access may lead to disruptions, unauthorized changes to processes, or even physical damage.
All those weaknesses lead to risks. OT systems typically involve a complex supply chain with components from various vendors. Supply chain risks, such as compromised components or malicious software, can introduce vulnerabilities into the OT infrastructure. Limited visibility into OT networks and processes makes it difficult to detect abnormal activities or security incidents. Inadequate monitoring can result in delayed detection of cyber threats and make it challenging to respond effectively.
How Does MQTT Help Mitigate Cybersecurity Attacks?
MQTT addresses the security challenge head-on, providing a secure and efficient means of data exchange. From its minimalistic design to its robust security mechanisms, MQTT is tailored to the unique demands of industrial environments, where reliability and security are not just preferences but necessities. MQTT enhances industrial security with its support for SSL/TLS encryption, reliable message delivery through Quality of Service (QoS) levels, and advanced features like Last Will and Testament (LWT) for heightened security awareness.
Potential Security Attacks on an MQTT Broker
Attacks on an MQTT broker can be varied and sophisticated. Here are some common types of attacks:
Eavesdropping/Interception: Since MQTT can transmit data in plain text, attackers can intercept this data to gain unauthorized access to sensitive information.
Man-in-the-Middle Attacks: Attackers can position themselves between the broker and the client to intercept or alter the messages.
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks: These involve overwhelming the broker with a flood of messages, thereby disrupting service for legitimate users.
Spoofing: Attackers can impersonate legitimate devices or clients to send malicious messages to the broker.
Insecure Authentication: If the broker does not enforce strong authentication mechanisms, attackers can gain unauthorized access.
Injection Attacks: Injecting malicious payloads into the messages can lead to various attacks, including command injection or SQL injection if the MQTT messages interact with a database.
Topic Hijacking: Since MQTT uses topics for message filtering, attackers can subscribe to topics they should not have access to, or publish messages to topics to spread misinformation.
Retained Message Manipulation: Attackers can publish malicious messages with the 'retain' flag, causing the broker to hold and disseminate harmful messages to new subscribers.
Brute Force Attacks: Attempting to gain access by repeatedly trying different passwords or keys.
To mitigate these threats, it's crucial to implement robust security measures like strong encryption, secure authentication, access control, and regular security audits. Also, check out our article Mitigate IoT Attacks with Key MQTT Security Principles for more information.
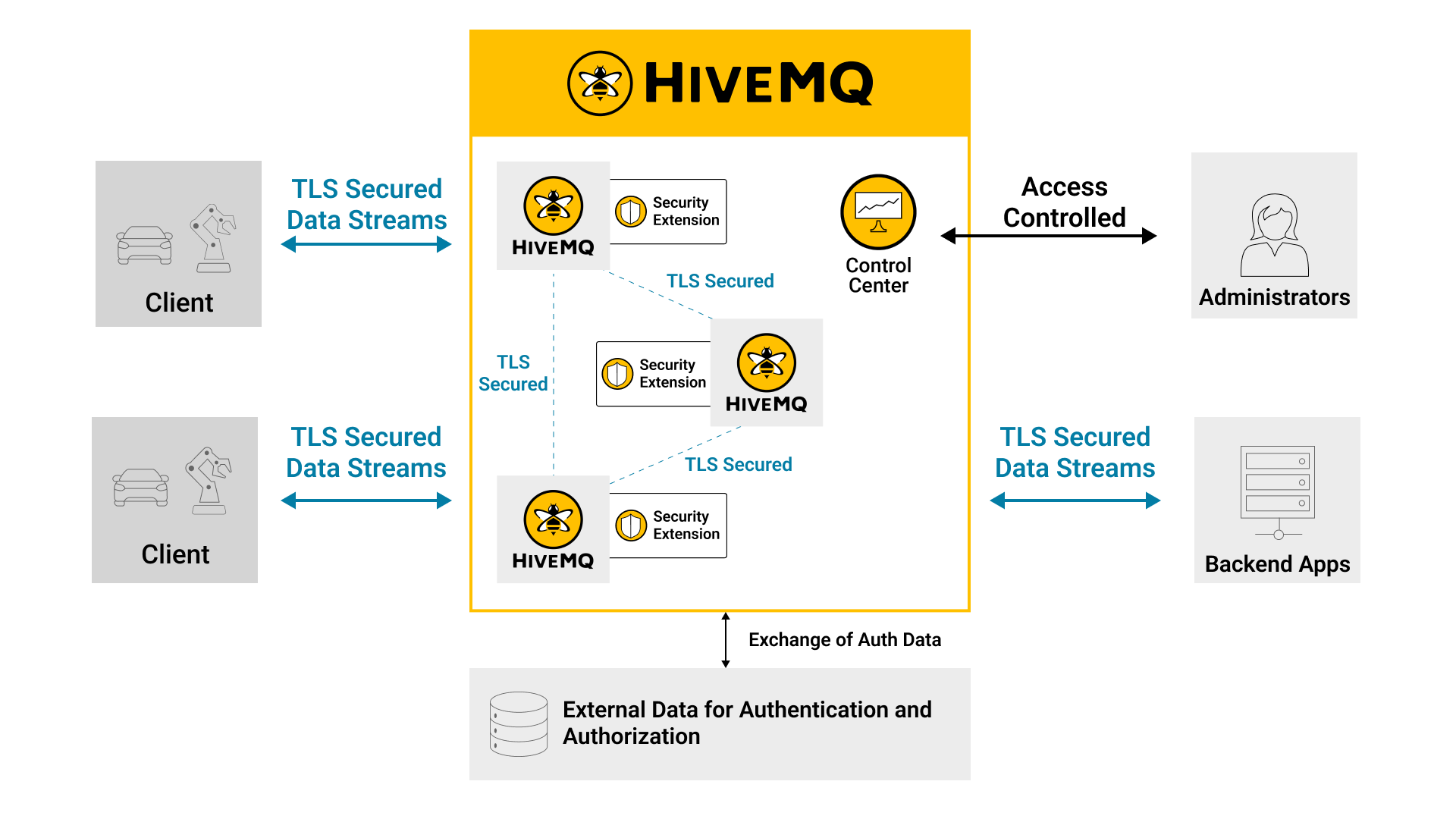
What is the Added Value of HiveMQ in Cybersecurity?
HiveMQ is a popular MQTT broker that provides enhanced security features for MQTT implementations. It is designed to secure MQTT deployments, particularly in large-scale and enterprise environments. Here's how HiveMQ adds security to MQTT:
TLS/SSL Encryption: HiveMQ supports TLS (Transport Layer Security) and SSL (Secure Sockets Layer) for encrypting data in transit. This ensures that the data exchanged between the MQTT clients and the broker is protected against eavesdropping and tampering. Verifying the server certificate is also a good way to mitigate man-in-the-middle attacks.
Client Authentication: HiveMQ allows for strong client authentication mechanisms. Besides the standard username and password authentication, it can integrate with external authentication systems such as OAuth, JWT, LDAP, client certificates or custom-built systems. This ensures that only authorized clients can connect to the MQTT broker.
Access Control Lists (ACLs): HiveMQ can use Access Control Lists to define granular permissions for different clients. This means you can control which MQTT topics a client can publish to or subscribe from, enhancing the security by ensuring clients have only the necessary access.
Bridge Security: For connecting multiple MQTT brokers (bridging), HiveMQ provides secure bridging capabilities. This means data exchanged between different brokers can also be encrypted and authenticated, ensuring security across distributed environments.
Secure Default Settings: HiveMQ is designed with security in mind, meaning many of its default settings are geared towards a secure deployment. This reduces the risk of insecure configurations.
Logging and Monitoring: HiveMQ provides extensive logging and monitoring capabilities, which are crucial for detecting and responding to security incidents. This enables a proactive approach to security management.
High Availability and Scalability: While not directly a security feature, HiveMQ's focus on high availability and scalability ensures that security doesn't come at the cost of performance, even in large-scale deployments.
Extra Considerations in the Design
While HiveMQ provides security mechanisms and functionality to protect your architecture, there are other considerations to take into account to ensure the overall security of the platform:
Payload Encryption: Apply payload encryption to the MQTT protocol for additional security in untrusted MQTT environments1.
Message Data Integrity: Use digital signatures/MACs, and checksums for MQTT messages1.
Securing MQTT Systems at Different Layers: Secure MQTT systems from the infrastructure level, at the operating system level, and at the MQTT broker level1.
Firewall: All connections to an MQTT broker should go through at least one firewall3.
It's not an exhaustive list, but it's a good starting point for building a secure platform on which to build use cases such as Industry 4.0, smart cities, and many others.
Wrap up
The integration of MQTT, particularly with the enhanced security features provided by HiveMQ, represents a significant stride forward in addressing the unique cybersecurity challenges of Operational Technology systems. By marrying MQTT's lightweight and efficient design with HiveMQ's robust security enhancements, industries are better equipped to safeguard their data transmission processes against the growing array of cyber threats. Furthermore, HiveMQ's scalability and high availability, coupled with its proactive monitoring and logging capabilities, empower industries to maintain a strong security posture without compromising on performance, even in large-scale and complex environments.
As industries continue to navigate the complexities of cybersecurity in the realm of OT, the role of MQTT and platforms like HiveMQ becomes increasingly vital. They not only provide a framework for secure communication but also signify a proactive approach to cybersecurity, ensuring that industrial environments are not just reactive in the face of cyber threats but are equipped to anticipate and mitigate them effectively. This evolution in industrial cybersecurity, driven by MQTT and HiveMQ, marks a pivotal shift towards a more secure, efficient, and resilient industrial future.

Anthony Olazabal
Anthony is part of the Solutions Engineering team at HiveMQ. He is a technology enthusiast with many years of experience working in infrastructures and development around Azure cloud architectures. His expertise extends to development, cloud technologies, and a keen interest in IaaS, PaaS, and SaaS services with a keen interest in writing about MQTT and IoT.
